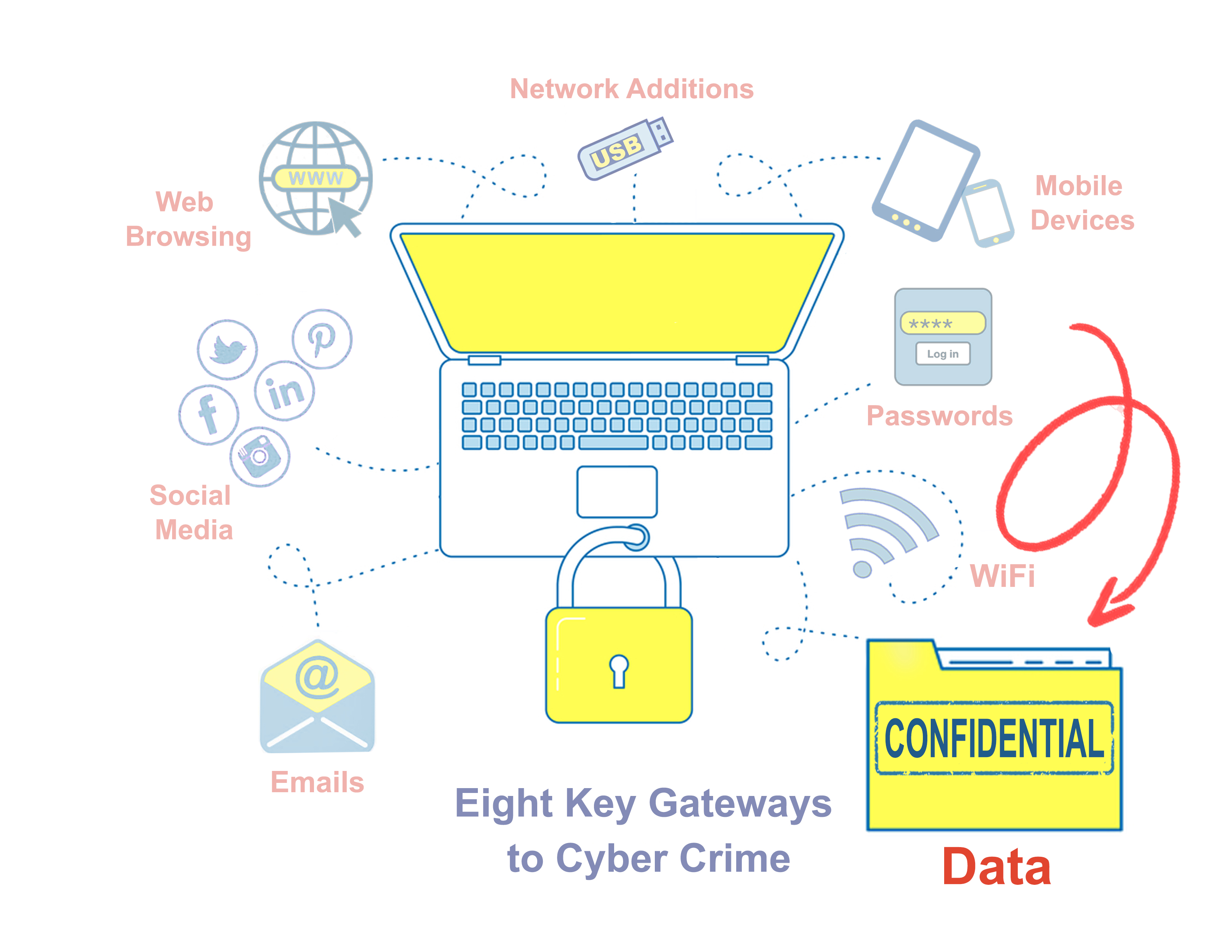
This is the third in a series of articles focusing on practical ways to block key Cyber Crime Gateways.
Data is the key to any organization’s success--yet many business owners neglect to implement basic best practices for data security. How are you doing? Can you answer these 7 questions? Do your answers coincide with best practices? If there is room for improvement, give us a call. We can help.
1. What data do you have?
Identifying sensitive data is the first step to keeping it safe. Take a look at all the data you hold, build the most comprehensive list of data possible, and record where it is stored. Consider data held on central servers, laptops, staff computers, smart phones, memory sticks, CRM’s or project management systems. What data is stored in the cloud or stored outside your business by third-party vendors such as your website host?
2. How valuable is this data?
Determine how sensitive each type of data is to your business. Data that provides customer records and their accounting and financial information should be the highest priority for security. This can include social security, driver’s licenses, health information, credit card and bank accounts. Mission-critical data can include your employee records, financial records, account records, sales insights and sales contracts, intellectual property and trade secrets. If data is classified as confidential, it should be clearly indicated within the data and/or on the user interface of the system used to access it. A label could state: "Confidential information and property of XYZ Corp. No part of these materials may be copied, used or disclosed except with written permission of XYZ Corp."
3. Who has access to your data?
Consider who accesses your data and how often. Ensure that each employee has access only to the data they need. This minimizes the chance of information being accidentally changed, deleted, compromised or lost. Your accounting team doesn’t need access to job applications; your HR team doesn’t need access to accounting records. Give each staff member their own username and password and grant different levels of access in Windows, your CRM and other business software.
Establish a “need-to-know policy” so even if an employee has clearance for a level of confidentiality, information is shared only if it is required for a specific task. Access rights are defined by involvement in assignments.
4. Is your data storage secure?
Storing data centrally is generally more secure. Storing it in a safe cloud solution combined with a virtual private network (VPN) allows secure, easy access for your team no matter where they are. Invest in a multi-user cloud platform, which gives employees their own usernames and passwords and provides full accountability and greater security. Consider using two-factor authentication wherever it is available and use encryption to protect your most important data.
Note: Having data in a single place reduces risk of theft, but also means there is a single point of failure. Having a reliable cloud or hybrid-cloud backup solution is critical to secure data storage.
5. How is your data shared?
How is data transferred in your business--by email, streamed online, uploaded to USB drives? A reputable cloud-based file sharing platform, designed for business, provides a secure transfer of information. For added security choose a sharing platform that allows you to restrict saving or printing the file and that revokes access after a specified period of time. If it is necessary to send sensitive data across the internet, always encrypt before sending.
6. How do you dispose of data?
When you move a file to the Recycle Bin is the file deleted? No, the only thing that’s changed is the location of the file. Make it a practice to empty the recycle bin regularly. But also, be aware that deleting data from the Recycle Bin does not immediately delete it—this only eliminates the file’s link to a name so that space is free to use again, but the file is still there until other data overwrites and replaces it. To ensure sensitive information is not recoverable, choose a secure wipe method. Also note, when you delete a file from cloud storage, it will be stored as long as you designate. Adept Solutions can help you navigate options to eliminate sensitive data permanently.
7. Have you trained your team on data best practices?
Does everyone in your organization understand the importance of data security? Everyone who has access to the data must take responsibility for its security. Implementing an Acceptable Use Policy that details what is and isn’t acceptable use of your data can be key in setting expectations for your team. Management should update the policy as needed and it should be reviewed and signed at least yearly by your entire staff. Consider assigning a security officer within your organization to oversee ongoing user online security training and/or Best Practices reminders in staff meetings and email blasts. Adept Solutions can help you develop your employee IT security program.