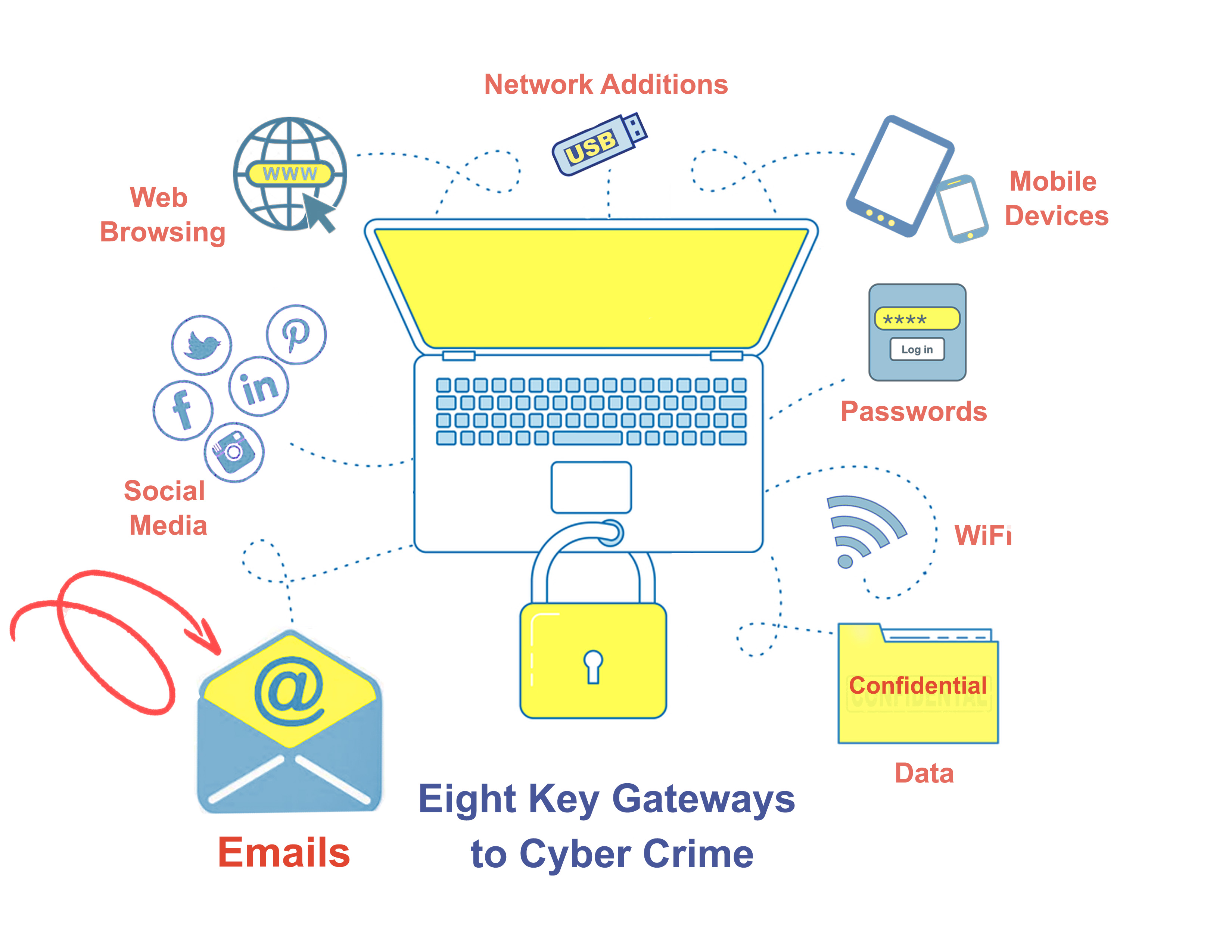
This is the fourth in a series of articles focusing on practical ways to block key Cyber Crime Gateways.
Email can be an open invitation for cyber criminals to breach valuable company data and steal personal identities. Don’t be a victim! Start the new year by giving up lazy habits that can compromise your success.
Bad Habit Count Down:
#5. Using your work email for personal purposes and/or personal email for work purposes.
Think Hillary Clinton. We may not have state secrets hidden in our emails, but privacy is still an issue--for you personally and for your company. Your employer has the right to monitor all traffic to and from their company programs and have the right to wipe devices if necessary. You can even go a step further and keep your email accounts on separate devices.
The more traffic on the account, the more opportunities for a clever cyber breach. Consider even using multiple private accounts such as one for communicating with family and friends; one for online shopping; one for newsletters, etc. A wise email user never puts all their “eggs in one basket.”
#4. Accessing company email from public wi-fi connections.
When working remotely or on a personal device, use VPN software to access corporate email. Unsecured WiFi connections are open invitations to cybercriminals. They can gain public access to the system and view any traffic you send or receive, which means they’ve gained access to your account.
#3. Sending personal information in an email message.
There are numerous places email data can be compromised and once sent, it can never be removed. Never assume emails are private or confidential. Emailed sensitive company information should be encrypted. Call us for information on how to do this! Don’t fall for scammers posing as vendors, banks, government sectors and other official looking entities. Reputable businesses never ask for personal information via email.
#2. Clicking, clicking, clicking.
Don’t click on attachments or links in emails—ever, ever, ever. Unless . . .
- You know the sender and were expecting the email and know what the link and/or attachment is.
- You know the sender, but weren’t expecting the email and you hoover over the link and see the URL is legitimate. Even better, open a browser and manually type in the address.
- You know the sender, but weren’t expecting the email and you are able to scan the attachment before opening. Contact us if you need to know more about scanning attachments or identifying legitimate URLs.
#1. Number One Habit to Leave Behind—LAME PASSWORDS!
Easy to guess passwords are like gold to hackers. Little nuggets with big returns. Use strong passwords that mix upper and lower-case letters, numbers and special characters, and change them often. Use a different password for each of your accounts—that way if one account is hacked, your other accounts are still safe. Using a password manager can be your best friend in helping you conquer the lame password habit.