There’s a good reason why businesses like Office 365: It’s a feature-rich productivity suite that gets plenty of upgrades throughout the year. Last month, Microsoft announced four new upgrades that will make the cloud platform even more irresistible for small- and medium-sized businesses.
Microsoft adds new Office 365 apps for SMBs
Enterprises features in Windows 10 update

The Windows Fall Creators Update released in April introduced many useful and interesting features, including a decluttered Start menu, more control over Windows updates, and an enhanced Microsoft Edge browser. Five months later, Microsoft follows up on all those enhancements with a new set of features.
It’s time to redefine the word “hacker”

When a cyber security researcher stopped the spread of WannaCry, the headlines praised him as a savior. But just a few short months later he was in handcuffs for allegedly creating a piece of malware that steals banking information. Even if he is innocent, it’s important to understand the difference between white hat, black hat and even gray hat hackers.
Cyber Crime Gateways—Is Your Team Ready to Defend Your Data?
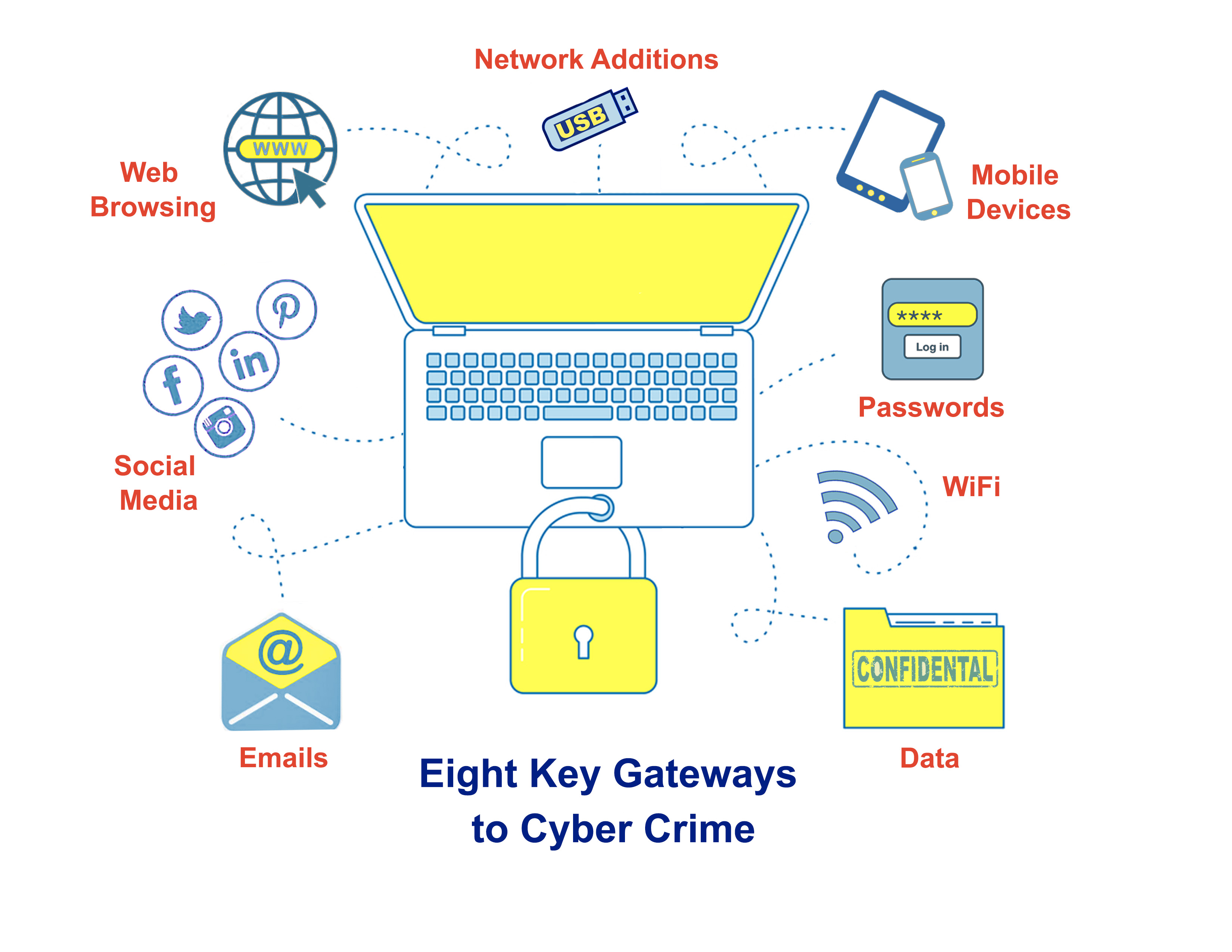
How can your data be compromised? Let us count the ways! The above eight areas of everyday work life can quickly become open invitations for cyber mischief if your team is not armed with Best Practices.
Our monthly newsletters feature security tips and articles to add to your team’s education, however, Best Practices are best learned through an ongoing Security Training Program within your company.
Why Should You Be a Partner Instead of a Client?
CEO article: How Can Technology Help Your Business—Right Now, part 2

Last month I talked about two ways technology can help you be a key contributor in your industry: sharing files in the cloud, and increasing teamwork through collaboration. While each of these features are technology based, they are also part of the innovation that is transforming our business environment.
Google’s 2-Step Verification sign-in
How to make the most of your CRM

Customer relationship management (CRM) software is essential for every marketing, sales, and customer service department. It allows you to capture your customers’ information and keep a record of their interactions with your business. If you’re new to the concept of CRM, here are some tips and tricks to help you get the most out of it.





