People rely on email to do a wide array of tasks. We use it to sign up for websites, apply for jobs, make payments, get in touch with friends and family, and many more. However, email is also commonly exploited by hackers to steal information or launch malware attacks.
Helpful tips for keeping your email safe
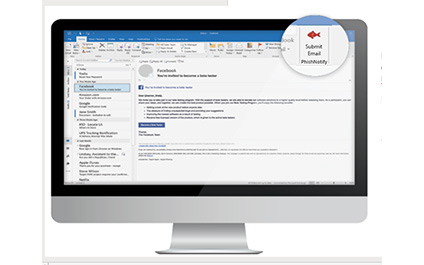
Get a Red Phish and IT Security Training
You open your inbox and nestled among the usual emails from vendors, clients, and employees is an email you weren't expecting.
It is from a friend you haven't heard from in a long time, and he is writing to ask a favor. Suspicious, right? But how do you know for sure it is a phishing attempt?
If you had a red phish in your email menu, you wouldn't have to wonder.
Hackers Love a Crisis!

The adage "never let a good crisis go to waste" applies to hackers everywhere. And the Coronavirus is the perfect crisis to exploit.
Sophos, one of Adept's security vendors, reports on one Coronavirus scam. They explain, "The fake page consists of the official, current home page of the World Health Organisation (WHO), with an unassuming popup form on top of it.
Phishing e-mails and how to spot the scams

What is Phishing?
“Good things come to those who bait.” This is true for fishing and unfortunately true for phishing, also. Phishing uses email as bait, with messages that appear to be from legitimate companies or from people you know.
These emails often appeal to human emotions such as:
Fear—an email from your “bank” saying your account has been compromised.
Understanding HTTPS

Many internet users still do not understand what the padlock icon in their web browser’s address bar is for. It represents HTTPS, a security feature that authenticates websites and protects the information users submit to them. This is an important feature that lets users know whether the site they are visiting is secure or not.
How Office 365 deals with phishing attacks

There are plenty of things to love about Office 365. For a small monthly fee, it gives you the latest cloud-based version of Microsoft Office apps and robust communication tools that improve collaboration and productivity. But it’s also an extremely secure platform that can defend against the most cunning phishing attacks.
Beware of these social engineering tactics
PhishPoint attack looks like SharePoint
Gearing up for phishing scams in tax season

As tax season looms, so do phishing scams. For cybercriminals, this is the ideal time of year to deceive unsuspecting individuals into releasing sensitive private or company information. Businesses must therefore take extra precautions between now and April 17th to avoid hackers from selling your confidential data in the dark web.
Safe web browsing requires HTTPS

Very few internet users understand the meaning of the padlock icon in their web browser’s address bar. It represents HTTPS, a security feature that authenticates websites and protects the information users submit to them. Let’s go over some user-friendly HTTPS best practices to help you surf the web safely.
- 1
- 2



