Social media phishing attacks are on the rise, with Facebook being one of the most commonly impersonated brands. Hackers are now employing more sophisticated tactics to steal personal data from social media users. To keep your data safe from them, heed our reminders and tips to strengthen your privacy settings and keep bad actors away.
Safeguard your social media accounts from hackers
Helpful tips for keeping your email safe
What is Cyber Resilience and Why Do You Need It?

CEO Article by Larry Johnson
The Olympics have just finished, and we have had some examples of great performances in the Tokyo games. I watched as two USA wrestlers were down to the last seconds when they won their matches. Gable Stevenson was down to less than 2 seconds when he came back to win, and David Taylor had less than 14 seconds when he won his match.
Get a Red Phish and IT Security Training
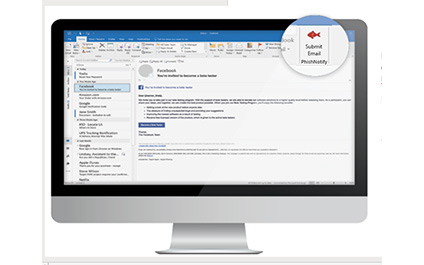
You open your inbox and nestled among the usual emails from vendors, clients, and employees is an email you weren't expecting.
It is from a friend you haven't heard from in a long time, and he is writing to ask a favor. Suspicious, right? But how do you know for sure it is a phishing attempt?
If you had a red phish in your email menu, you wouldn't have to wonder.
Threats facing financial institutions today

The financial sector has long been heavily targeted by cybercriminals. Over the years, the number of attacks that involved extortion, social engineering, and credential-stealing malware has surged rapidly. This means that financial institutions should strive to familiarize themselves with the threats and the agents behind them.
Understanding HTTPS

Many internet users still do not understand what the padlock icon in their web browser’s address bar is for. It represents HTTPS, a security feature that authenticates websites and protects the information users submit to them. This is an important feature that lets users know whether the site they are visiting is secure or not.
Turn off Windows 10’s invasive settings

Advertisers are able to target their consumers more effectively thanks to social media. But did you know that your operating system might also be giving away information about your online searches to advertising agencies? Learn more about Windows 10's not-so-private settings and how these can be fixed.
Fileless malware: The guileful threat

Over the past few years, the security industry has been witnessing a rapid evolution in attack techniques, including fileless malware, which uses legitimate tools and services such as existing software, applications, and authorized protocols to carry out malicious activities such as unauthorized data retrieval or data damage.
Invaluable tips for online safety

You probably go to great lengths to keep yourself safe, whether at home or in public. But what happens when you get online? Learn more about how you could be exposing yourself and your personal information over the internet so you can stay safe.
With the headlines about data breaches and cyberattacks greeting you every time you go online, it seems impossible to have a surefire, foolproof way to keep your information secure.



